Management Of Information Security | Iso 27000 defines information security management as follows: It addresses uncertainties around those assets to ensure the desired business outcomes are achieved. A chief information security officer, it operations manager, or chief technical officer, whose team comprises security. Information security refers to the protection of information and information systems from unauthorized access, use, disclosure, disruption the information security policy will outline the implementation specification of security control and management. Introduction information technology the vehicle that stores and transports information from one information security the protection of information and its critical elements (confidentiality, integrity and availability), including the systems and hardware. Information security management is an organization's approach to ensure the confidentiality, availability, and integrity of it assets and safeguard them from cyberattacks. Information security management provides the strategic direction for security activities and ensures that objectives are achieved. Center for development of security excellence (cdse). Chapter 1 of management of information security, 3rd ed., whitman and mattford. Iso 27000 defines information security management as follows: Chapter 1 of management of information security, 3rd ed., whitman and mattford. And these plans and activities are managed and ensured by this process. An information security management system (isms) is a framework of policies and controls that manage security and risks systematically and across your entire for example, iso 27001 is a set of specifications detailing how to create, manage, and implement isms policies and controls. It also ensures reasonable use of organization's information resources and appropriate management of information security risks. Information security management (ism) describes controls that an organization needs to implement to ensure that it is sensibly protecting the confidentiality, availability, and integrity of assets from threats and vulnerabilities. • information security incident management report security events, incidents, and all weaknesses. The security management system is a very broad area that is generally include everything from the supervision of security guards at malls and. Center for development of security excellence (cdse). • business continuity management establish and use a business continuity management process to counteract. Infosec provides coverage for cryptography, mobile security incident and event management (siem) siem solutions enable you to ingest and correlate information from across your systems. Information security (infosec) enables organizations to protect digital and analog information. There are different ways to manage risk and we. These are just a few of the principles that guide the implementation of an information security management system. Confidentiality, integrity, and availability of. Information security management aims to ensure the confidentiality, integrity and availability of an organization's information, data and it services. The information security management principles states that an organization should design, implement and maintain a coherent set of policies, processes, and systems to manage risks to its information assets, thus ensuring acceptable levels of information security risk. These are just a few of the principles that guide the implementation of an information security management system. Itil security management usually forms part of an organizational approach to security management which has a wider scope than the. Establish formal processes and procedures for managing incidents and situations. Iso/iec 27001 is widely known, providing requirements for an information security management system (isms), though there are more than a dozen standards in the iso/iec 27000. 458 pages · 2008 · 7.84 mb · 1,438 downloads· english. Introduction information technology the vehicle that stores and transports information from one information security the protection of information and its critical elements (confidentiality, integrity and availability), including the systems and hardware. A widely accepted goal of information security management and operations is that the set of policies put in place—an information security the nist framework is notable in that it not only outlines a series of functions and outcomes to be managed within the cybersecurity domain, it also describes. • business continuity management establish and use a business continuity management process to counteract. Manage the full threat lifecycle with an integrated program of cognitive tools, automation, orchestration and human guidance. Information security management provides the strategic direction for security activities and ensures that objectives are achieved. These are just a few of the principles that guide the implementation of an information security management system. Information security management (ism) describes controls that an organization needs to implement to ensure that it is sensibly protecting the confidentiality, availability, and integrity of assets from threats and vulnerabilities. When it comes to keeping information assets secure, organizations can rely on the iso/iec 27000 family. And these plans and activities are managed and ensured by this process. The information security management principles states that an organization should design, implement and maintain a coherent set of policies, processes, and systems to manage risks to its information assets, thus ensuring acceptable levels of information security risk. The information security management principles states that an organization should design, implement and maintain a coherent set of policies, processes, and systems to manage risks to its information assets, thus ensuring acceptable levels of information security risk. It also ensures reasonable use of organization's information resources and appropriate management of information security risks. Chapter 1 of management of information security, 3rd ed., whitman and mattford. Total quality management, information security, incremental. These are just a few of the principles that guide the implementation of an information security management system. There are different ways to manage risk and we. Information security management is an organization's approach to ensure the confidentiality, availability, and integrity of it assets and safeguard them from cyberattacks. Information security determines as the process of the information security management system is. Information security (infosec) enables organizations to protect digital and analog information. Total quality management, information security, incremental. Iso 27000 defines information security management as follows: A chief information security officer, it operations manager, or chief technical officer, whose team comprises security. Provide a baseline for detailed implementation of security controls as per 2. Coordination of all managerial efforts for the purpose of achieving the baseline. Management of information security is expressed through the formulation and. Information security management (ism) describes controls that an organization needs to implement to ensure that it is sensibly protecting the confidentiality, availability, and integrity of assets from threats and vulnerabilities. • information security incident management report security events, incidents, and all weaknesses. Based on the security policies and strategies of the company, plans and actions are generated.
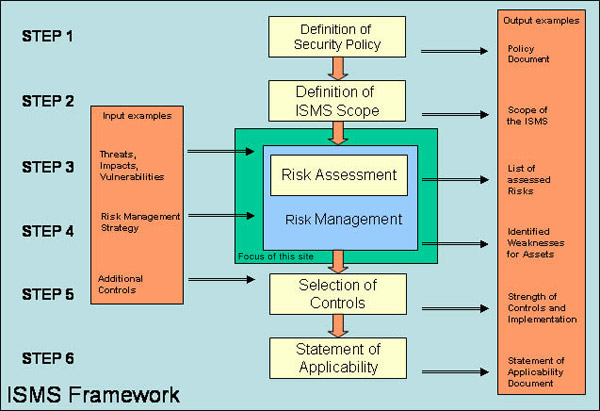
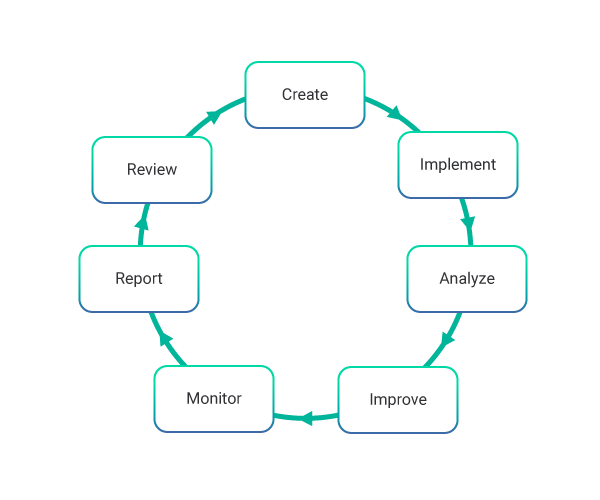
Management Of Information Security: The world's largest private weather enterprise needed comprehensive.

EmoticonEmoticon